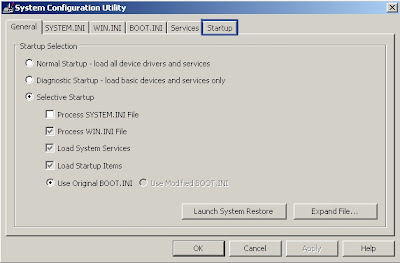
Windows comes with a System Configuration Utility installed. This utility can be used to disable malware items from starting up. Generally, if malware does not launch at start up it does not run at all. While disabling the infection removes none of it, your job will be easier without the malware being in control of your computer while your effort at removal is underway. To use the System Configuration Utility to this end:
- Go to your start page
- Click Start. Your Start Up Menu will deploy.
- Click Run. A pop-up window wil appear.
- Type "msconfig" in pop-up window.
- Click OK. The System Configuration Utility window will appear.
- Click Start Up tab.
- Scroll to find offending program.
- Click on program name to remove check-mark from box.
- Click Apply.
- When you exit the System Configuration Utility you will be prompted to restart your system.
- Click Restart.
- Your system will be in "Selective Restart mode" so long as a start up item is disabled.
Many malware products are designed to be hidden, from or to disable, the System Configuration Utility, it is true, but it is certainly worth checking to see if your computer's infection is listed or not. If your System Configuration Utility will not deploy it is a good bet that your malware infection has disabled it in order to prevent being removed.
If your infection has registered on your machine as a Browser Helper Object (BHO), and you have a recent version of the Internet Explorer Browser, it should appear as an entry in Explorer's Manage Add Ons utility. Your Explorer toolbar may be hidden in the most recent versions. If so, press the Alt button on your keyboard and it will appear. When the toolbar is displayed, in order to Manage Add Ons:
- Click Tools.
- Roll your mouse-pointer down to the "Manage Add Ons" entry.
- Click Enable or Disable Add Ons
- Click on name of add on to be disabled. The item will be highlighted, as a result.
- Click Disable
- Click OK.
By no means are all malware infections registered as BHOs. Nor is it clear how many may be programmed to interfer with the operation of the Manage Add Ons utility. Again, it is certainly worth checking to see if your computer's infection is listed or not. While disabling the infection removes none of it, your job will be easier without the malware being in control of your computer while your effort at removal is underway.
What may be able to remove at least most of your infection is Window's Add or Remove Program utility. To remove a program by the Add or Remove Programs:
- Click Start
- Click Control Panel
- Click Add or Remove Programs. Wait for the list of programs to load.
- Click name of program to be removed.
- Click Change Remove (You may be offered the opportunity to click on Support Information if available to learn more about the program you are removing).
Most malware will not appear in your Add or Remove Programs utility but some adware companies do include an uninstall feature for their software in this area. It is important to remember that the uninstall may still leave tracking and other passive files in your computer. After removal you should check your start up listing with the System Configuration Utility. If you do not find it listed, you should check your start up listing using HijackThis and/or scan your system with your preferred anti-virus scanner(s).

